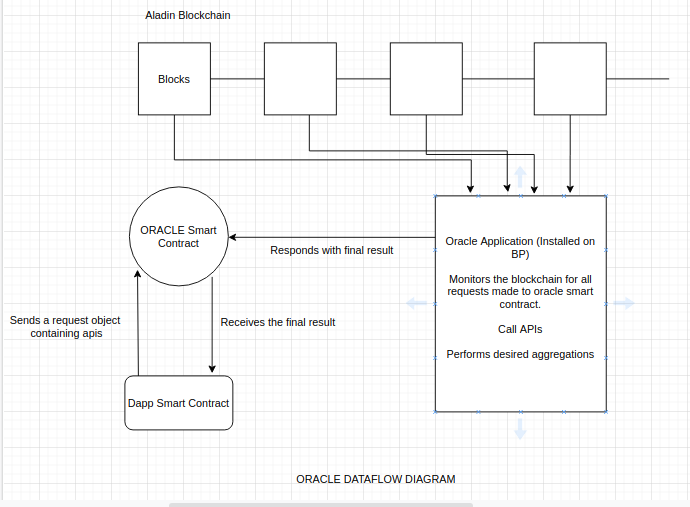


From a mythological perspective, oracles were the medium through which humans sought knowledge about things they couldn’t comprehend. That is somewhat similar to the role oracles play for blockchains.
Blockchain is a new technology that holds the potential to revolutionise various industrial processes. There have been various breakthroughs in blockchain but still, most human processes occur outside of the blockchain world. And blockchains, by design, are detached from the outer world, which makes them incapable of reading data that we create outside of the blockchain ecosystem.
Hence, if we want to use blockchains as a mainstream technology, we need a system that can help blockchains read and store data from other sources as well. And an oracle is such a system.
Oracles translate outside data such that blockchains and its applications can understand and respond to a given input. At present, the most dominant use of oracles is seen in helping blockchain-based smart contracts initiate predefined actions on the basis of data received from the outside world.
Based on where oracles get the data input from and how they feed the data into the blockchain, they can be classified as:
- Software oracles,
- Hardware oracles,
- Consensus-based oracles,
- Inbound oracles, and
- Outbound oracles
What vulnerabilities do oracles face?
Oracles are an indispensable part of innovation through blockchain as they tremendously increase the potential use cases of the technology. However, they also bring certain vulnerabilities that we need to overcome.
Let’s take a look.
Freeloading
The nodes of an oracle network need to reach consensus before data is fed to a blockchain network. These nodes may sometimes copy the answer of other nodes, causing the third-party oracle to feed biased data to the blockchain. This is called freeloading.
Majority attack
The most feared attack in a decentralised network is a majority attack. It happens when a majority of the nodes know each other or one entity holds a significant voting power and they exercise that power to manipulate the end result. Doing so, they can easily tamper with the data provided to the blockchain.
Data corruption
In case we use only one oracle, we define a single point of failure for attackers. With only one data source to verify the truth, ill actors can easily corrupt the data for their benefit.
Risk to on-chain data confidentiality
Using an oracle means engaging a third party to handle people’s data. It is possible that even though the oracles provide encrypted data, they may disclose the original request made by a user. This puts the security of users’ data at risk.
How does Alacrity Integrated Oracle overcome these vulnerabilities?
Unlike other blockchains that rely on third-party oracles, Alacrity Network has built an integrated and universal oracle for the Alacrity Network. This renders the blockchain network security against any chances of manipulation caused by third party nodes. Alacrity Oracle creates another security layer by shuffling its oracle nodes upon each new request, which ensures no set of nodes can together plan and carry out an attack on the system.
Besides, Alacrity Oracle is capable of working with data from every industry while most oracles can only do so with specific industries. And the network uses a shared software package that gives oracle nodes the authority to pass on the data without making them capable of altering with it.
Providing a publically available audit trail is another feature of Alacrity Oracle that helps make the flow of data through the network more transparent and secure.
These salient features of the Alacrity Integrated Oracle place it above other available oracles in the industry in terms of on-chain and off-chain security, transparency, and interoperability.

Leave a Reply